Supply Chain Attacks and their impact on OT/ICS Cybersecurity
Solarwinds and other supply chain attacks are the initial attack vector on organizations – the first link in a sequence of steps to achieve control and disruption. How can industrial networks be protected?
Described by Microsoft’s President Brad Smith as the world’s largest and most sophisticated cyber-attack, the Solarwinds (Sunburst/Solorigate) hack was, in fact, just the beginning of an attack sequence. As with other Supply Chain attacks, Solorigate was the initial attack vector on organizations, an entry point to establish a foothold on the target’s network.
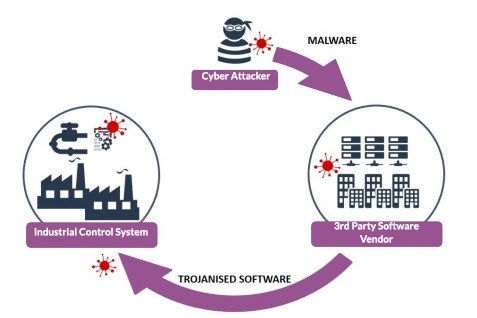
While there have been extensive articles on the technical mechanisms, and indications of compromise (IOCs) of Solorigate, most literature and analysis of the attack end at that. The ultimate target of the threat actors wasn’t delivering the trojanized Orion software update. The goal was using its remote access capabilities to initiate an attack sequence inside of the organization.
Solarwind – OT impacts
Discovered in December 2020, the timeline of the Solarwinds attack dates back to at least September 2019, allowing attackers to carefully select high-value targets and launch its primary sequence of privilege escalation, lateral movement, data exfiltration and other malicious activities.
Among these high value targets are Industrial organizations. An analysis of the thousands of domains impacted by Sunburst indicates that over 32% belonged to manufacturing, utilities, and other critical enterprises. To emphasize, while Orion is an IT infrastructure monitoring platform, the intention of the attackers in these targets was most likely the propagation into and the impact of their ICS networks.
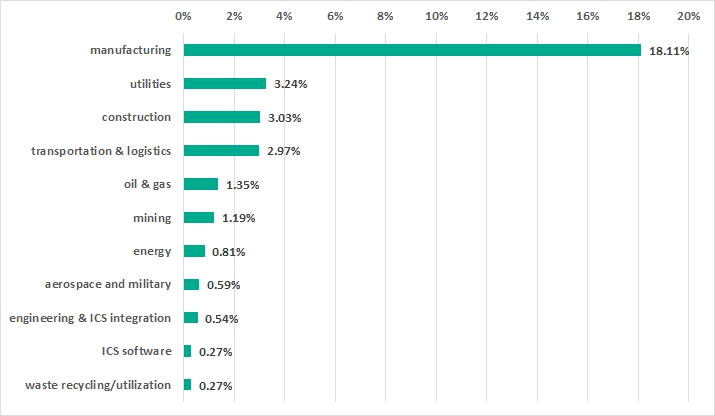
Breakdown of Industrial organizations impacted by Solorigate of the total of impacted enterprises:
Manufacturing companies were a top target
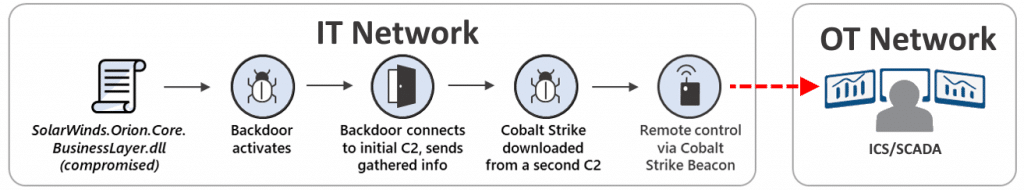
Once inside the target’s IT network, attackers deploy a back door enabling remote hands-on control through their C2 (Command & Control) servers, enabling network weaknesses discovery, often using a modification of the Cobalt Strike pen-testing tool. The weaknesses discovered then provide the means for lateral movement into the organization’s OT/ICS network segments.
Breakdown of Industrial organizations impacted by Solorigate of the total of impacted enterprises:
Manufacturing companies were a top target
Entry into the industrial network opens a variety of options, with an alarming pattern being “wiper” Ransomware attacks. Multiple companies were recently hit, including the WastedLocker attack against the smartwatch manufacturer Garmin, reportedly paying $10 million, and Foxconn being demanded a $34 million ransom. Both organizations experienced enterprise-wide encryption, leading to disruption of manufacturing operations. The acute sensitivity of ICS assets to downtime makes these organizations a prime target since even brief shutdowns can cause millions in losses.
What can be done?
To prevent these attacks, Industrial organizations must deploy a comprehensive layered security approach directed at securing OT networks:uk
- If your organization is using Solarwinds, perform a comprehensive forensic investigation to ensure your network was not compromised and has been cleaned of malicious activities.
- Build security into your supply-chain and other 3rd party applications used by your organization, including a strict review of all updates in a controlled environment.
- Deploy multiple security layers including firewalls, web/browsing, email/phishing, supply chain file uploads , endpoint security, and other controls. Ensure the solutions are updated and properly configured.
- Ensure all operating systems and applications are patched for vulnerabilities. Update access policies and passwords on all services with a dedicated review for all internet-facing applications.
- Perform periodical penetration tests including breach attack and lateral movement simulations.
- Prevent file-based attacks on the IT network by securing the organization’s trusted content transfer routes.
- Map the organization’s OT/ICS assets and periodically scan appliances to ensure their protection.
- Apply strict IT to OT network segmentation and air-gap critical assets.
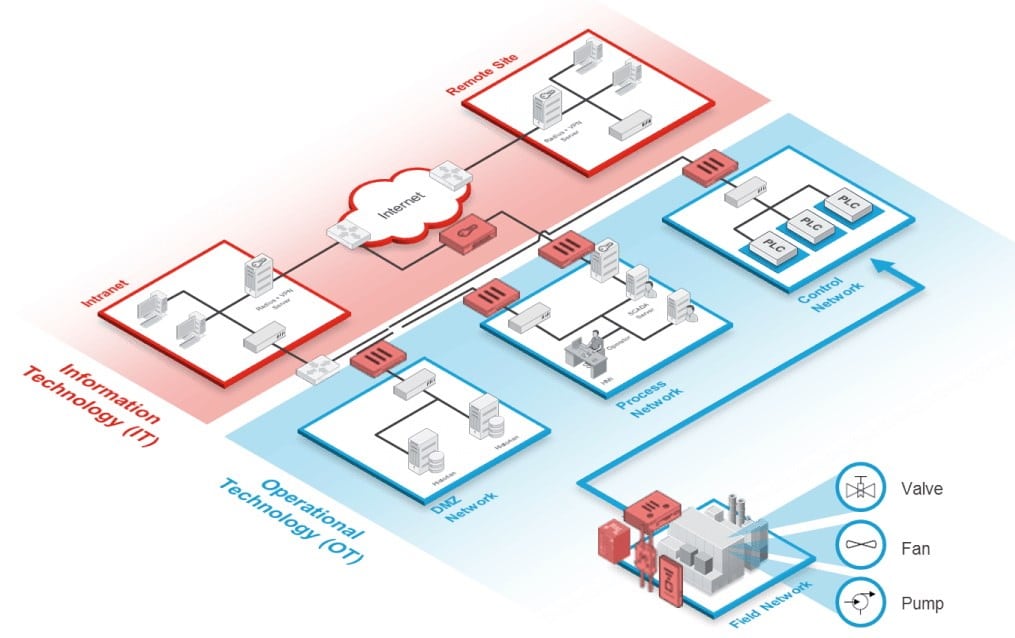
IT-OT convergence requires multi-layered
security with strict control of files allowed into the OT network
How GateScanner will help
GateScanner offers a wide suite of solutions to prevent attacks on OT networks:
- Ensures the security of third-party software updates using GateScanner’s deep threat scans including NextGen detection.
- Prevents file-based attacks on the IT environment by using Content Disarm and Reconstruction, protecting multiple content routes, including email security, secure browser downloads, and content sharing. GateScanner sanitizes Excel files, MS word files, emails and hundreds of other file types.
- Prevent lateral movement into the OT network by applying network separation, enforces data transfers using data-diodes.
- Provides security and visibility on outgoing content by apply redaction (DLP) security policies.
- Ensures cyber physical security for OT ingestion of removable (USB) devices, appliances, and other TCAs (Transient Cyber Assets), enabling NERC CIP and NIST compliance.
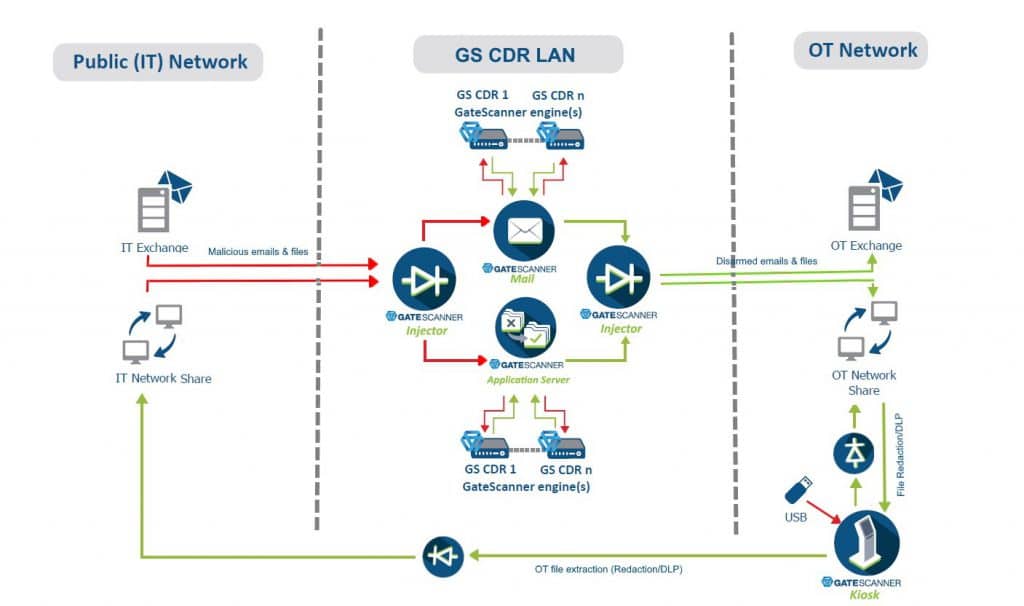
GateScanner protects multiple content routes,
preventing file-based attacks on OT networks
An incident is inevitable but should never be a catastrophe. The Solarwinds attacks illustrated the extensive efforts malicious actors use to gain access into organizations. While alarmingly complex, the attack is only one of many methods to initiate a sequence that will disrupt the organization. Industrial enterprises are highly targeted and at significant risk. They must deploy the means to prevent the initial file based attack on their IT infrastructure, and prevent incident propagation into their critical OT environment.
Contact Sasa Software today for a FREE demo to experience how we can secure your operations.
Tags/Keywords:
Supply Chain Attacks, IT/OT, ICS Security, Solarwinds, Sunburst, Solorigate, SIndustrial Cybersecurity, OT security, Content Security, Network Separation, Business Email Compromise, Network separation, Lateral movement, Cross-domain solutions, Content disarm and Reconstruction, CDR, Sasa Software, GateScanner
Image credits: sasa-software.com , microsoft.com, fortinet.com , kaspersky.com, cybertalk.org , infinitygroup.co.uk

