
Gartner, the world’s leading research and advisory company, recently published the Hype Cycle for Threat-Facing Technologies, 2019[1], identifying Content Disarm and Reconstruction (CDR) on the Peak of Innovation phase of the Hype Cycle.
Gartner Hype Cycle, Gartner, Inc., 2017
As mentioned in the report, “CDR, which is also referred to as ‘content sanitization’, breaks down files into their discrete components; strips away anything that doesn’t conform to that file type’s original specification, ISO standard, or company policy; and rebuilds a ‘clean’ version. This near-real-time process is an effective approach to removing malware and other exploits from files. While sandboxing and almost all other techniques depend on detection, CDR protects against exploits and weaponized content that have not been seen before.” Gartner has also identified CDR with a “high” benefit rating.
The CDR process disrupts the integrity of any remaining hidden malicious code, zero-days, or exploits. The result is a visibly identical, functional and completely safe (harmless/neutralized), new copy of the original file.
According to Gartner, “by 2022, Gartner expects 20% of organizations to use CDR as part of their content protection strategies, up from 5% today. We also expect CDR to be available as a standard capability everywhere multiple antivirus scanning is deployed.”
We believe this is because CDR overcomes the shortcoming of technologies such as signature-based AV, NextGen AI-based detection and behavioral analysis sandboxing. All of these technologies rely on a decision-based process which can ultimately fail and are prone to evasive techniques used by attackers. CDR offers tangible benefits that outperform sandboxing in almost all aspects- it is easier to implement, quicker, handles much larger volume/ higher throughput, and unlike traditional technologies, it doesn’t rely on detection. CDR can mitigate one of the common infection vectors- scripts embedded in MS-Office and PDF documents, that can be highly obfuscated, which a significant challenge for many security solutions that rely on static scanning. It can also neutralize sophisticated, sandbox-evading malware that can delay operation for as long as it being held in a virtual environment.
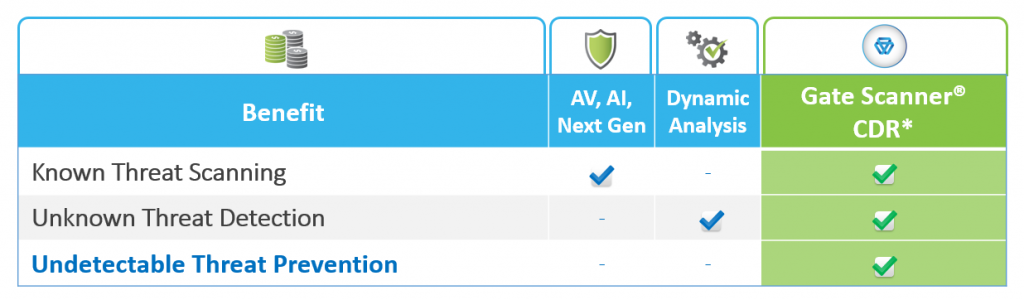
AVs, NGAVs, and Sandboxing all rely on a decision-making process when analyzing a file – either static or dynamic. This process can ultimately fail. CDR is the only technology that doesn’t rely on detection.
An important differentiator of the Sasa Software GateScanner® CDR is that the technology integrates best of breed scanning and detection technologies, including NGAVs (NextGen AVs) and Sandboxing as a preliminary phase. Yet, GateScanner® CDR understands that a “clean” answer by these technologies indicates that a threat hasn’t been found, so still treats the file as suspicious, applying proprietary file disarm technologies, supporting the widest range of file-types available.
Sasa Software has established itself as a CDR market leader, which isn’t surprising given the fact that GateScanner® CDR was originally developed in 2010 to protect Plasan, a defense contractor supplying armored vehicles to the US DoD. In late 2013 Sasa Software spun off from Plasan to commercialize the technology and now secures hundreds of sensitive networks and critical facilities.
Summary
Malware hidden in documents is such a common attack vector, responsible for many destructive attacks of recent years, and there is an inability of sandbox and other signature-based solutions to successfully handle such malware.
[1] Gartner “Hype Cycle for Threat-Facing Technologies, 2019” by Pete Shoard, 12 July 2019. Gartner subscribers can review the report here.
Disclaimer
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.

