
Sandbox environments often face challenges related to performance overhead and scalability. The process of analyzing potential threats within a sandbox can consume significant system resources, impacting overall system performance. Additionally, as the volume of threats and data increases, the scalability of the sandbox environment becomes a concern.
Implementing resource throttling and prioritization within the sandbox environment can help mitigate performance overhead and scalability issues. By allocating resources based on the criticality of the analysis and the workload, the sandbox can optimize its resource usage.
One technology that can be used to effectively decrease the amount of data that needs to be processed by the sandbox is Content Disarm and Reconstruction (CDR). CDR, a powerful anti-malware technology, essentially extracts content from content files and delivers it in new and threat-free copies.
Positioning CDR engines before the sandbox can significantly minimize the volume of data that requires sandboxing. CDR achieves similar, if not better levels of threat mitigation, on non-executable data. The CDR engines should be configured to pass on to sandbox only those files that are designated executables, while disarming all other incoming files with CDR, thus reducing the load significantly on the sandbox.
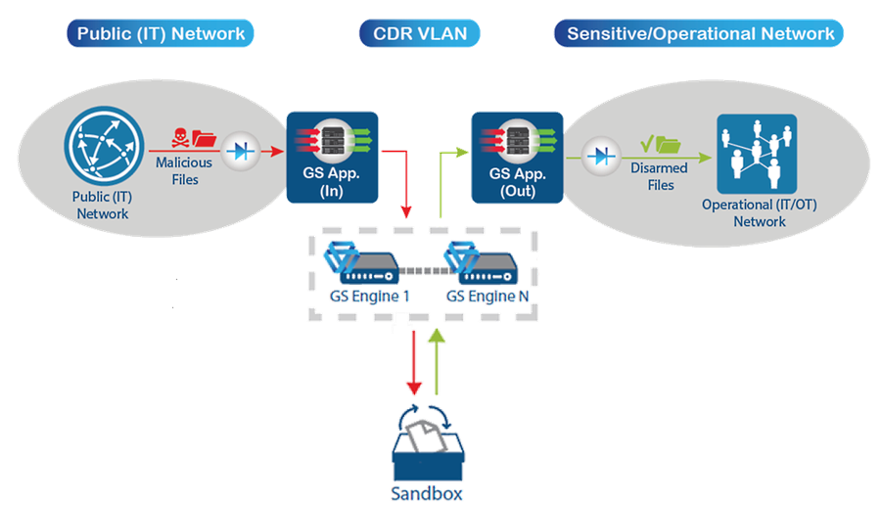
Example of CDR-Sandbox integration: Sandbox is inserted into a GateScanner CDR Multi-source flow
Dealing with Advanced Threats
Despite the effectiveness of sandbox environments in detecting and isolating various types of malware, advanced threats can sometimes evade detection and analysis within the sandbox. These threats may employ sophisticated techniques to avoid triggering the security measures in place.
For example, a type of advanced threat known as a “polymorphic malware” is designed to constantly change its code and appearance to evade traditional detection methods. Within a sandbox environment, such malware may alter its behavior in real-time, making it challenging for the sandbox to accurately identify and analyze its malicious activities.
Utilizing machine learning and artificial intelligence algorithms within the sandbox environment can enhance the detection of advanced threats. These algorithms can adapt and learn from new evasion techniques, improving the sandbox’s ability to identify and analyze sophisticated threats.
Here too, CDR anti-malware technology can help. As it does not rely on detection, it is capable of blocking known and unknown threats hidden in non-executable files, with equal ease. Placing a CDR solution, such as through an API service, before the sandbox, can greatly reduce the risk of advanced threats ever reaching the sandbox.
Contextual Awareness
Sandboxes operate in isolated environments and may lack a comprehensive understanding of real-world systems. This limitation can lead to false positives or negatives, where the sandbox incorrectly identifies benign activity as malicious, or vice versa.
A sandbox environment analyzing a legitimate software application may mistakenly flag it as malicious if it lacks contextual awareness about the typical behavior of that specific application within a real-world system. This can result in a false positive, indicating a threat where none exists.
Incorporating context-aware analysis by considering the behavior of applications and files in real-world scenarios can mitigate false positives and negatives. By building a comprehensive understanding of normal behavior, the sandbox can better differentiate between benign and malicious activities.
Zero-Day Exploits
Like other systems, sandboxes are vulnerable to zero-day exploits involving the sandbox software and all applications installed within its environment.
It is crucial to continuously update the sandbox’s components and update it with information on emerging threats and analyzing behavioral patterns, so that the sandbox can proactively identify and respond to previously unknown vulnerabilities.
Enhancing Sandbox Technology
Introducing dynamic analysis augmentation, such as behavior-based detection, can enhance the sandbox’s capabilities to combat evolving threats effectively. By continuously evolving the analysis techniques, the sandbox can adapt to new threat patterns and behaviors.
Another approach is to Leverage advanced deception techniques, such as honeypots and deceptive files that can help in outsmarting advanced threats within the sandbox environment.
For example, a sandbox environment may use behavior emulation to simulate user interactions with a potentially malicious file, observing how the file interacts with the system without posing an actual risk. Deception techniques can involve creating virtual environments that appear enticing to threats, ultimately exposing their behavior for analysis without posing a real threat to the actual system.
While sandbox technology is indispensable in cybersecurity, it requires meticulous strategic enhancements to comprehensively address its inherent limitations. By understanding and strategically overcoming these challenges, cybersecurity defenses can be effectively fortified.

