In cybersecurity, detecting and mitigating threats posed by malicious executable code within benign files is a significant challenge.
The 2020 SolarWinds breach exemplifies the damage caused when trusted software updates are compromised, leading to widespread cyber intrusions across government and corporate networks.
Malicious executables often remain undetected until activation, as seen in the SolarWinds incident, where the infiltration went unnoticed for nine months. Sandboxing, while useful, is resource-intensive and can be evaded by sophisticated malware.
Static binary analysis is an emerging threat assessment approach. By reverse-engineering code, it provides insights into executables without triggering harmful actions. Analysts can scrutinize execution paths, data structures, and system interactions, resulting in a risk score that identifies high-risk content.This methodology strengthens defenses by examining executable content to preempt threats. It enhances security measures and builds confidence in safeguarding digital assets.
Sasa Software’s GS Analyzer upgrade for the GateScanner suite reverse-engineers compiled executable code in over 120 file types, identifying threats and scoring overall risk. This score automates binary file filtering, allowing administrators to inspect high-risk files while passing low-threat ones.
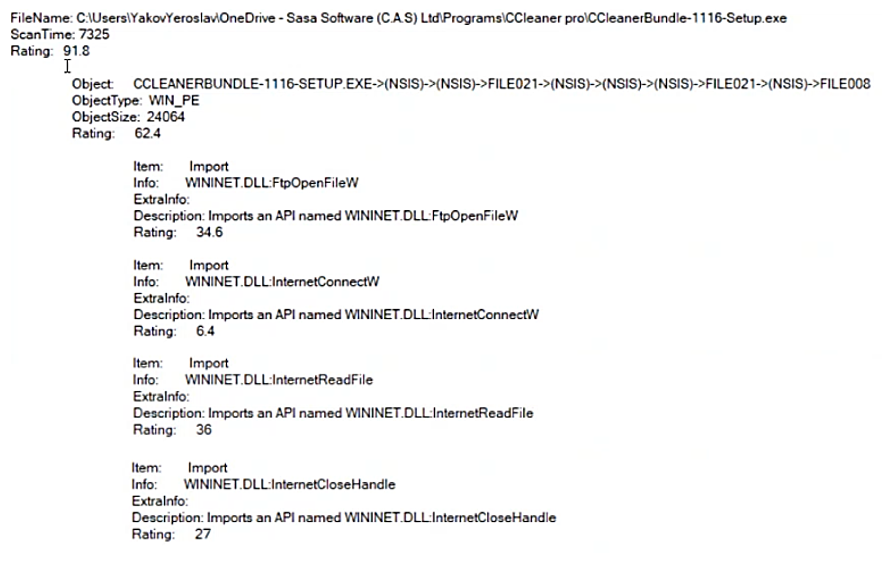
The following snippet shows a sample of GS Analyser code analysis and threat ratings of a CCleaner Pro’s setup file:
Malicious executables often remain undetected until activation, as seen in the SolarWinds incident, where the infiltration went unnoticed for nine months. Sandboxing, while useful, is resource-intensive and can be evaded by sophisticated malware.
Static binary analysis is an emerging threat assessment approach. By reverse-engineering code, it provides insights into executables without triggering harmful actions. Analysts can scrutinize execution paths, data structures, and system interactions, resulting in a risk score that identifies high-risk content.This methodology strengthens defenses by examining executable content to preempt threats. It enhances security measures and builds confidence in safeguarding digital assets.
Sasa Software’s GS Analyzer upgrade for the GateScanner suite reverse-engineers compiled executable code in over 120 file types, identifying threats and scoring overall risk. This score automates binary file filtering, allowing administrators to inspect high-risk files while passing low-threat ones.
The following snippet shows a sample of GS Analyser code analysis and threat ratings of a CCleaner Pro’s setup file:
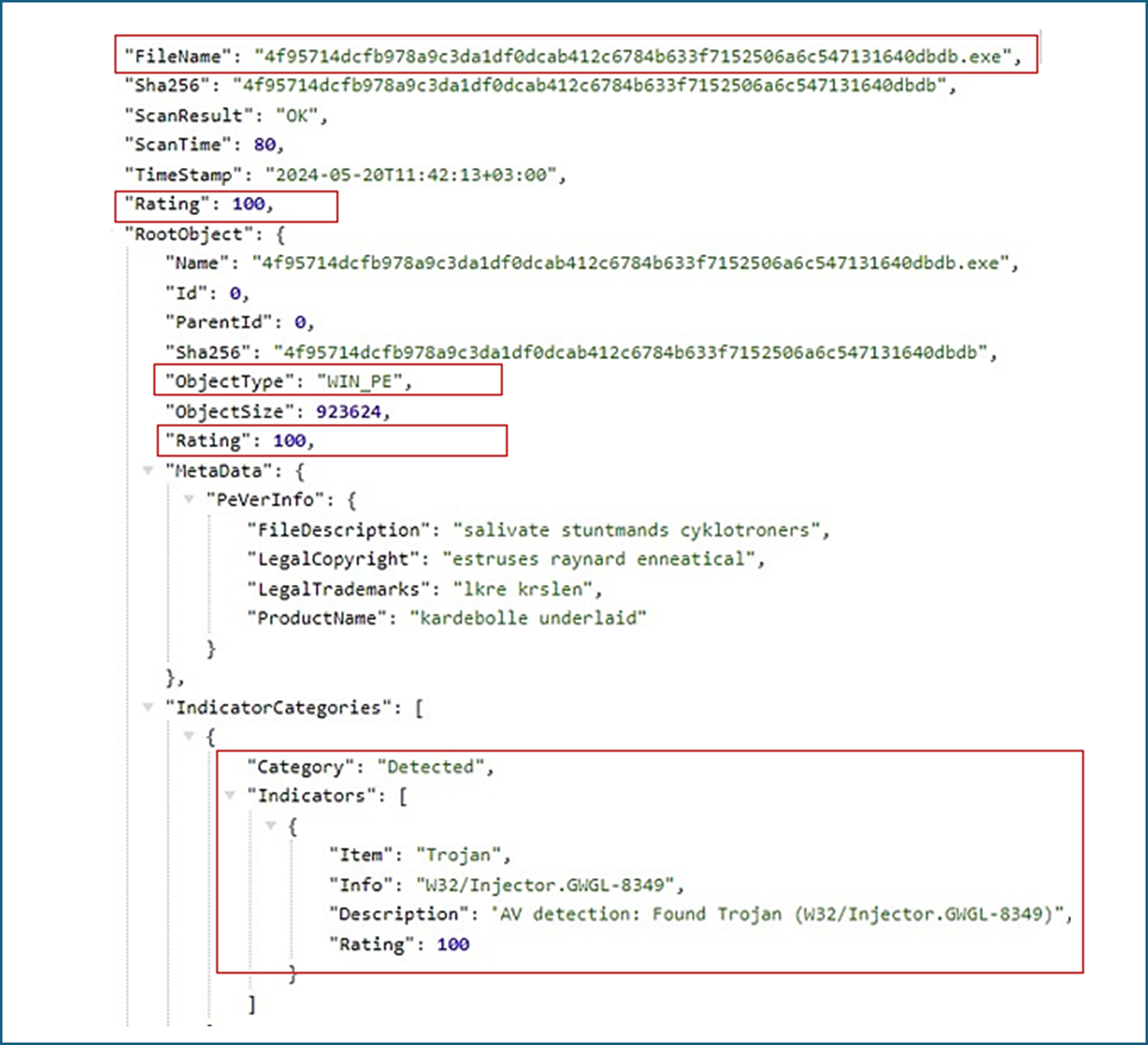
The following example shows a GS Analyzer code analysis and threat detection in a decompiled executable file:
Download the GS Analyzer product page
For more information on GS Analyzer contact info@sasa-software.com
For more information on GS Analyzer contact info@sasa-software.com
Keywords: Malicious Binaries, Macros, Cybersecurity, Static Code Analysis

