Blog: Secure Your Digital Infrastructure
Blog
Shai-Hulud and the 2025 NPM Supply-Chain Worm: What the New Waves Mean — and Where CDR Fits In
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
When the Lights Go Out: The Hidden Risk of Zero-Day Attacks Timed With AV Update Blackouts — and Why Offline-Deterministic Protection Is Now Essential
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
Supply Chain Threats Inside Legitimate Content Feeds: An Escalating Cybersecurity Challenge
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
Code Embedded in Multimedia and Interactive Files: The New Malware Frontier
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
Encoded Malware in PDFs and Document Annotations
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
Ransomware Surge on SMBs: How Small Businesses Are Facing Big Threats and How GateScanner CDR Mitigates Them
As cybersecurity professionals gather for GovWare 2025, file-based threats remain one of cybersecurity’s most persistent “black holes.” Learn how intelligent threat elimination is revolutionizing file security.
Microsoft Teams Impersonation: How Matanbuchus 3.0 Is Delivered via Collaboration Tools — and How CDR Defeats It
As cybersecurity professionals gather for GovWare 2025, file-based threats remain one of cybersecurity’s most persistent “black holes.” Learn how intelligent threat elimination is revolutionizing file security.
Weaponized PDFs: How the new “MatrixPDF” toolkit works — and why native CDR stops it
As cybersecurity professionals gather for GovWare 2025, file-based threats remain one of cybersecurity’s most persistent “black holes.” Learn how intelligent threat elimination is revolutionizing file security.
What is a Zero-Day Exploit? Understanding the Hidden Cyber Threat
As cybersecurity professionals gather for GovWare 2025, file-based threats remain one of cybersecurity’s most persistent “black holes.” Learn how intelligent threat elimination is revolutionizing file security.
What Is a Polymorphic Virus? The Shape-Shifting Malware Threat
As cybersecurity professionals gather for GovWare 2025, file-based threats remain one of cybersecurity’s most persistent “black holes.” Learn how intelligent threat elimination is revolutionizing file security.
What Is Network Security? Your Complete Protection Guide
As cybersecurity professionals gather for GovWare 2025, file-based threats remain one of cybersecurity’s most persistent “black holes.” Learn how intelligent threat elimination is revolutionizing file security.
What is Operational Technology (OT)? A Complete Guide for 2025
As cybersecurity professionals gather for GovWare 2025, file-based threats remain one of cybersecurity’s most persistent “black holes.” Learn how intelligent threat elimination is revolutionizing file security.
What is Ransomware? Understanding the Modern Cyber Threat Landscape
As cybersecurity professionals gather for GovWare 2025, file-based threats remain one of cybersecurity’s most persistent “black holes.” Learn how intelligent threat elimination is revolutionizing file security.
Navigating the Last Frontiers of File-Based Cybersecurity
As cybersecurity professionals gather for GovWare 2025, file-based threats remain one of cybersecurity’s most persistent “black holes.” Learn how intelligent threat elimination is revolutionizing file security.
What are Executables and Why Are They a Threat?
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
Phishing Prevention Best Practices
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
Protect Your Company with Cloud Email Security
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
The Fundamentals of Data Redaction
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
What is Data Masking? A Complete Guide to Data Protection
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
What is Detection Evasion?
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
What is a Data Diode?
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
What are Cross Domain Solutions?
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
What is a Data Breach and How to Prevent It?
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
Advanced Persistent Threat: The Silent, Long-Term Cyberattack
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
The File-less Malware Misconception: Why “No Files” Doesn’t Mean No Malicious Files
File-less Malware Header MISCONCEPTION ALERT File-less ≠ No Files Why “file-less” malware still uses malicious files → MemoryPayload The term “file-less malware” has become a cybersecurity buzzword, often accompanied by dramatic claims about attacks that exist purely in memory without touching the disk. While this technology represents a significant evolution in attack techniques, the terminology
When a Picture Is Worth a Thousand Threats: The Hidden Dangers in PNG Files and the Power of Deep Content Inspection
Explore how attackers use innocent-looking PNG images to bypass traditional security and how deep content inspection (CDR) can prevent these stealthy threats.
Choosing the Right Email Security Solution: A Head-to-Head Comparison
In the ever-evolving landscape of cyber threats, email remains one of the most targeted and vulnerable attack vectors. Organizations looking to harden their defenses often turn to specialized email security solutions—but with so many options on the market, how do you choose the right one? Let’s break down key takeaways from a comparison of four
Spam Filter Gateway: The First Line of Defense Against Modern Email Threats
Spam Filter Gateway Banner Spam Filter Gateway: First Line Defense Essential cybersecurity infrastructure creating protective barriers between external email threats and internal systems. Filters malware, phishing, and social engineering attacks before reaching employee inboxes. Primary Attack Vector Protection – Email Security 99.9% Blocked Real-time Multi-layer Email Secured Spam filter gateways have become essential components of
Network Segregation: Building Resilient Security Architecture for the Modern Enterprise
Network Segregation Banner Network Segregation: Strategic Isolation Cornerstone of modern cybersecurity architecture. Compartmentalized network resources provide robust defense by containing breaches and protecting critical digital assets from sophisticated threats. Beyond Perimeter Security – Intelligent Containment Critical Finance HR Data Public Guest Segmented & Secure Network segregation has emerged as a cornerstone of modern cybersecurity architecture,
Business Email Compromise (BEC): Why These Social Engineering Attacks Are Costing Companies Millions
BEC Surgical Precision Banner BEC: Surgical Precision Targeted research. Personalized deception. Authentic urgency. Unlike broad phishing nets, BEC attacks are methodically crafted. Most Financially Damaging Cybercrime High Threat Business Email Compromise represents a growing threat to organizations worldwide, fundamentally different from traditional cyberattacks. Rather than exploiting technical vulnerabilities, BEC attacks manipulate human psychology and trust
Advanced Persistent Threat (APT): The Silent Cyber Predators Every Organization Must Understand
Introduction As we advance through 2025, the cybersecurity landscape is witnessing an unprecedented evolution in malware threats. The emergence of adaptive malware—malicious software enhanced with artificial intelligence capabilities—represents a paradigm shift in how cyber attacks are conducted and defended against. Unlike traditional malware that follows static, pre-defined instructions, adaptive malware continuously learns, evolves, and adapts
Unpacking the Threat: How Email Deconstruction Supercharges Virus Detection
Have you ever wondered what’s truly hidden inside the emails flooding your inbox?Beyond the visible text and attachments, emails are complex digital containers, often housing layers of hidden code and encoded content. This intricate structure, while facilitating rich communication, also provides a fertile ground for cyber attackers to conceal malicious payloads. To effectively combat these
Lumma Stealer: Unmasking the Invisible Thief and Fortifying Your Defenses
In the evolving cybersecurity landscape, polymorphic and metamorphic malware represent the elite class of threats that continuously transform themselves to evade detection. This adaptive behavior is their defining characteristic and the primary reason they pose such significant threats to organizational security. While both types appear similar on the surface—constantly changing to avoid detection—their underlying mechanisms and capabilities differ substantially. Let’s explore these sophisticated threats and how to defend against them.
Adaptive Malware: The AI-Powered Threat Transforming Cybersecurity in 2025
In the evolving cybersecurity landscape, polymorphic and metamorphic malware represent the elite class of threats that continuously transform themselves to evade detection. This adaptive behavior is their defining characteristic and the primary reason they pose such significant threats to organizational security. While both types appear similar on the surface—constantly changing to avoid detection—their underlying mechanisms and capabilities differ substantially. Let’s explore these sophisticated threats and how to defend against them.
Understanding Polymorphic Malware: The Encryption Masters
In the evolving cybersecurity landscape, polymorphic and metamorphic malware represent the elite class of threats that continuously transform themselves to evade detection. This adaptive behavior is their defining characteristic and the primary reason they pose such significant threats to organizational security. While both types appear similar on the surface—constantly changing to avoid detection—their underlying mechanisms and capabilities differ substantially. Let’s explore these sophisticated threats and how to defend against them.
Why Managed File Transfer Outperforms SFTP for Modern Business Security
The Evolving File Transfer Landscape In today’s digital business environment, secure file transfer capabilities have become mission-critical. Organizations exchange sensitive information with partners, customers, and across internal systems daily, often transferring gigabytes of data containing proprietary information, customer records, and other valuable assets. The stakes couldn’t be higher – according to recent data, the global
The AI Phishing Revolution: Implications for Cybersecurity in 2025
The Changing Face of Phishing Artificial intelligence has dramatically transformed the cybersecurity landscape of 2025. Where once phishing attacks were characterized by obvious grammatical errors and crude personalization attempts, today’s AI-powered phishing campaigns present a sophisticated threat that challenges traditional security measures. This evolution presents both unprecedented challenges and opportunities for organizations committed to protecting
Zero-Day Malware in 2025: Defending Against the Unknown
In today’s rapidly evolving threat landscape, zero day malware represents one of the most formidable challenges facing organizations worldwide. Unlike conventional threats that can be identified by signature-based detection methods, zero-day malware operates entirely below the radar—unknown to security vendors and undetectable by traditional scanning technologies. These sophisticated threats exploit the gap between malware innovation
Separating Substance from Marketing: What Makes File Security Truly Deep
In the cybersecurity industry, terminology often becomes a battleground where marketing creativity competes with technical reality. Recent years have seen the emergence of terminology suggesting certain Content Disarm and Reconstruction (CDR) solutions penetrate file structures more “deeply” than others. CDR technology, by its very nature, should always be thorough and comprehensive regardless of marketing qualifiers.
Fortifying the Perimeter: Static Code Analysis and CDR in a Layered Defense Strategy
In the face of increasingly sophisticated cyber threats, a layered security approach is paramount. While Content Disarm and Reconstruction (CDR) offers a robust method for sanitizing document-based threats by reconstructing files to eliminate active content, its efficacy is limited when dealing with executable files. Executables, by their nature, cannot be reconstructed without altering their fundamental operation,
Removable Media Malware Scanning Kiosks: A Comprehensive Approach to NIST Media Protection
Removable media devices represent a significant attack vector for organizations. USB drives, external hard drives, and other removable media can introduce malware, facilitate data exfiltration, or compromise network integrity if not properly secured. The National Institute of Standards and Technology (NIST) Special Publication 800-53 Revision 5 addresses these concerns through various media protection controls, notably
The Antivirus Multi-Scan Tradeoff: Striking the Right Balance
Antivirus (AV) solutions are the first line of defense against malware threats, offering essential protection against known attacks. Many organizations adopt AV multi-scanning, using multiple AV engines to increase detection rates and reduce reliance on any single vendor. But is more always better? This article explores the pros and cons of AV multi-scanning, the tradeoffs
What’s the Difference Between Firewalls and Data Diodes?
As cybersecurity threats become more sophisticated, organizations must deploy the most effective security measures to protect their critical networks. Two commonly used technologies—firewalls and data diodes—serve distinct purposes in network security. Understanding their differences can help organizations choose the right solution for their security needs. Background: Firewalls vs. Data Diodes The term firewall originates from
Mastering Network Segmentation A Guide For It Security Teams: Secure Your Digital Infrastructure
In today’s increasingly complex and fast-changing cyber threat environment, network segmentation is crucial for effective security measures. When implemented correctly, it can significantly reduce the risk of attackers moving laterally within the network, limit the impact of any breaches, and improve overall network performance and manageability. However, achieving effective network segmentation requires a thorough understanding

Gs Analyzer Meeting The Challenge Of Malicious Executables: Secure Your Digital Infrastructure
In cybersecurity, detecting and mitigating threats posed by malicious executable code within benign files is a significant challenge. The 2020 SolarWinds breach exemplifies the damage caused when trusted software updates are compromised, leading to widespread cyber intrusions across government and corporate networks. Malicious executables often remain undetected until activation, as seen in the SolarWinds incident,

Avoiding Data Diode Disasters Common Pitfalls And Their Mitigations: Secure Your Digital Infrastructure
Data diodes are the go-to solution for securing and segmenting critical networks however, faulty implementation could introduce vulnerabilities. In this post, we’ll explore common pitfalls in data diode implementation – how attackers have taken advantage of them and what you can do to avoid such instances in your network. Configuration Oversights The most obvious and

Strategic Technological Approaches To Minimize Supply Chain Vulnerabilities: Secure Your Digital Infrastructure
The modern supply chain landscape is a complex web of interconnected entities, spanning across borders and involving intricate digital and physical processes. While these supply chains facilitate global commerce, they also present inherent vulnerabilities and risks, especially in the realm of cybersecurity. In response to these challenges, organizations are increasingly turning to advanced technological strategies

Gatescanner Mail Gateway Receives Cybersecurity Award: Secure Your Digital Infrastructure
The winners of the 20th Annual 2024 Globee® Awards for Cybersecurity were announced today with Sasa Software named second in the Email and Web Security category, and first in email security. Sasa Software submitted its innovative GateScanner Mail Gateway solution for the protection of enterprise email, which for the first time offers Content Disarm and

Ai Powered Malware Preventing The Unknown: Secure Your Digital Infrastructure
Malware developers are leveraging AI algorithms to automate and enhance various stages of the attack lifecycle, from reconnaissance to evasion. This results in stealthier and more targeted attacks that can bypass traditional security measures. Conventional security tools struggle to detect AI-generated malware due to its dynamic and polymorphic nature. As a result, network security teams

Optimizing The Sandbox Recognizing And Addressing Limitations: Secure Your Digital Infrastructure
Sandbox technology, a crucial component in cybersecurity, grapples with intricate challenges that necessitate an in-depth understanding for effective mitigation. In this post we will review some approaches to meet current challenges facing this technology. Performance Overhead and Scalability Issues Sandbox environments often face challenges related to performance overhead and scalability. The process of analyzing potential

Safeguarding Medical Imaging Data Addressing The Orthanc Osimis Dicom Web Viewer Vulnerability: Secure Your Digital Infrastructure
Healthcare organizations rely heavily on DICOM (Digital Imaging and Communications in Medicine) technology for the storage and exchange of medical imaging data. However, a recent advisory from the Cybersecurity and Infrastructure Security Agency (CISA) has shed light on a critical vulnerability in the Orthanc Osimis DICOM Web Viewer, posing a significant threat to the security of medical imaging data. This

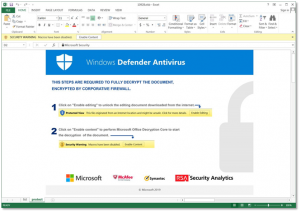
Addressing Security Risks in Digitally Signed PDF Documents
Digitally Signed PDF Banner 1011010 1100101 0110100 1110010 1001110 0101101 1010101 1100010 0111001 1010110 1100101 0110100 1011010 1100101 0110100 1110010 1001110 0101101 PDF Digitally Signed & Secure Authenticated • Encrypted • Verified VERIFIED✓ By Yakov Yeroslav, CEO One of the most formidable cyber threats today involves malicious actors exploiting trusted network channels to infiltrate organizations’

The Importance Of Central Management In Sheep Dip Kiosk Implementation: Secure Your Digital Infrastructure
USB drives, while convenient for data storage and transfer, can also introduce several inherent threats to computer systems and networks, such as malware and viruses, autorun exploits and firmware attacks. A commonly used security measure, known by the name “Sheep dip”, is the deployment of USB scanning kiosks. However, to truly maximize the effectiveness of

New Study From Cisa Cdr Reduces Risk Content In Files By 98: Secure Your Digital Infrastructure
New study from CISA: CDR reduces risk content in files by >98% In a recent study from the Cybersecurity and Infrastructure Security Agency (CISA) that was presented at RSAC 2023 [1], Tom Ruoff and Dr. Olga Livingston showed results of a pilot assessment model for anti-malware controls that tested three CDR solutions in a chained

New Threat In Rtf Files Cve 202321716: Secure Your Digital Infrastructure
Critical threat in RTF files (CVE-202321716) Microsoft recently announced a newly discovered vulnerability in RTF files that gives unauthenticated users access to remotely execute commands on host machines. An attacker could send a malicious e-mail containing an RTF payload that would allow execution of commands within the application that was used to open the malicious

Sasa Software Wins Award For Medical Imaging Data Security Solution: Secure Your Digital Infrastructure
Sasa Software Wins Award for Medical Imaging Data Security Solution February 26, 2023, Tel Aviv ‘People and Computers’, the leading Israeli IT portal, has announced its winners for the 2022 ‘Excellence in Computing’ competition, naming Sasa Software as an ‘IT Awards’ winner in the Command & Control category, for the new GateScanner Imaging Gateway that combines
SVG images – the hidden threat your anti-virus can’t see
SVG images – the hidden threat your anti-virus can’t see A new type of file-based attack is spreading quickly, cleverly circumventing standard detection-based protections. This method of attack employes malicious emails with HTML attachments that include embedded, base64-encoded, SVG images. SVG images can, by design, include Javascript tags, and these script tags are now being

Dicom Digital Imaging And Communications In Medicine Vulnerability Exposed: Secure Your Digital Infrastructure
[Updated January 2023] Recently detected activity of the CLOP ransomware gang involving the compromise and infection of medical imaging CD’s and the DICOM files within, has raised alarm due to the extremely wide exposure represented by this ubiquitous medium.Sasa Software is currently the only cybersecurity vendor offering a dedicated solution for the protection of healthcare networks

Hacking For The Millions The Dark Side Of Chatgpt: Secure Your Digital Infrastructure
Hacking for the Millions: The dark side of ChatGPT Hacking just got a lot easier. With ChatGPT, even novices can craft cutting edge malicious code with the power of an AI knowledge base. ChatGPT, which stands for Chat Generative Pre-trained Transformer, is a chatbot developed by OpenAI. Launched in November 2022, it has been heralded

Blocking The Raspberry Robin Usb Worm: Secure Your Digital Infrastructure
Blocking the Raspberry Robin USB Worm The Microsoft Security Threat Intelligence team recently reported the discovery of activity showing that the Raspberry Robin worm is now part of a complex and interconnected malware ecosystem with links to other malware families and alternate infection methods beyond its original USB drive spread. The investigators found that Raspberry

Sasa Software Named Top Infosec Innovator For 2022: Secure Your Digital Infrastructure
Sasa Software named winner of ‘Top Infosec Innovator’ for 2022 TEL AVIV, OCTOBER 27, 2022 – SASA SOFTWARE the cybersecurity industry’s leading provider of Content Disarm and Reconstruction (CDR) network security solutions today announced that is has been named a winner in the Top InfoSec Innovator Awards for 2022. Sasa Software competed against many of

Threat Alert / Critical Infrastructure: Avoslocker
| Threat Alert AvosLocker is a Ransomware as a Service (RaaS) affiliate-based group targeting critical infrastructure sectors globally, including, but not limited to, the Financial Services, Critical Manufacturing, and Government Facilities sectors. AvosLocker ransomware encrypts files on a victim’s server and renames them with the “.avos” extension. AvosLocker actors then place ransom notes on the

Gartner Cdr Content Sanitization Scores High In Network Infrastructure Security: Secure Your Digital Infrastructure
Gartner: CDR content sanitization technology scores high in network infrastructure security Content Disarm and Reconstruction (CDR) technology is identified by Gartner as a ‘high benefit’ technology for network infrastructure security as it continues to mature towards mainstream adoption. In the latest edition of Gartner’s Hype Cycle report on network security (July ’21)[1], content sanitization technology

Dicom The Invisible Vulnerability Of Healthcare Networks: Secure Your Digital Infrastructure
DICOM: The ‘Invisible’ Vulnerability of Healthcare Networks Attacks on healthcare systems are a growing concern. Healthcare data is a special category of sensitive data, containing extremely sensitive personal information that make it attractive both for institutional blackmailing – in the form of ransomware, and for individual ransom demands as in the case of high-profile individuals.
Gatescanner Secure Mail Gateway: Advanced Protection Strategies
On the Future of Email Security Introducing GateScanner Mail Gateway An interview with Yakov Yeroslav, CEO of Sasa Software Q: Sasa Software has been at the forefront of file-based cyber-protection for several years now, with the GateScanner USB Kiosk successfully installed in hundreds of locations around the world. What prompted Sasa Software to go ahead

GISEC Dubai – Live events are back!
GISEC Dubai – Live events are back! By Oren T. Dvoskin / Global Marketing Director @ Sasa Software Face to face meetings are back! We just returned from GISEC 2021– the Gulf’s leading Cybersecurity event. It was our first F2F event and our first business travel outside of Israel since #COVID. It truly dawned on me

Supply Chain Attacks And Their Impact On Ot Ics Cybersecurity: Secure Your Digital Infrastructure
Supply Chain Attacks and their impact on OT/ICS Cybersecurity Solarwinds and other supply chain attacks are the initial attack vector on organizations – the first link in a sequence of steps to achieve control and disruption. How can industrial networks be protected? Described by Microsoft’s President Brad Smith as the world’s largest and

Lessons Learned from the Oldsmar Water Treatment Cyber attack
Lessons learned from the Oldsmar water supply cyberattack Hacked: The water treatment facility in Oldsmar, FL According to a cybersecurity advisory issued jointly last Thursday (2/11) by the FBI, CISA, UEPA and the Multi State ISAC, unidentified cyber actors had obtained unauthorized access to the supervisory control and data acquisition (SCADA) of a U.S. drinking water

Gatescanner Salesforce Connector Brings Data Security To The Cloud: Secure Your Digital Infrastructure
GateScanner-Salesforce connector brings CDR data security to the cloud Sasa Software has teamed up with Assuta Medical Centers, Israel’s largest private medical services provider, and Deloitte Digital, the world’s leading professional services firm, to develop a Salesforce security software connector that deliver Salesforce content protection in a transparent, SaaS-based modality.GateScanner® Content Disarm and Reconstruction (CDR) Salesforce connector is

Avoiding Adrozek and other browser-modifier malware
Microsoft Security Research Team has recently reported (December 10) that a browser modifier malware they have named Adrozek has been widely observed in recent months. This malware affects multiple browsers, including Chrome, Edge, Firefox and Yandex Browser. The mechanism of attack is modifying browser settings and DLL files to result in injection of unauthorized ads

Emotet Campaign
Emotet Campaign – Guidance to GateScanner Users Emotet, one of the most famous and dangerous Trojans, has lately been spotted as a part of a mass phishing campaign. The campaign consists of an email which includes a Microsoft Office doc that when clicked gives an Office 365 error message, generated by an obfuscated macro script. The
Tackling Qbot and preventing ransomware attacks
Tackling Qbot and preventing Ransomware Attacks The infamous Qbot banking trojan has recently been spotted again, infecting tens of thousands of machines to date, mainly in the USAlso known as Quakbot, QakBot and Pinkslipbot, the Qbot trojan is a highly-maintained malware, with sophisticated evasion and persistence capabilities, and equipped with a worm-like functionality enabling it

Inside The Garmin Cyberattack Anatomy Of The Wastedlocker Ransomware: Secure Your Digital Infrastructure
Cyberattacks can be personal. Last Thursday, July 23rd, Garmin experienced a massive WastedLocker ransomware attack.
Read about what went behind the scenes.

Sasa Software Gartner Cool Vendor: Secure Your Digital Infrastructure
Sasa Software named “Cool Vendor” by Gartner, in Cyber-Physical Systems (CPS) Security report 2020. Analyst firm Gartner recently published the “Cool Vendors in Cyber-Physical Systems Security” (CPS) [1] naming Sasa Software in the report. This adds to a previous publication, “Market Guide for Operational Technology Security” [2], identifying Sasa Software in the OT Endpoints Security

Gdpr Stand Aside Meet Ccpa: Secure Your Digital Infrastructure
The interactions between CCPA compliance and Security solutions
Effective Jan 2020, CCPA has implications beyond GDPR.
Do your security solutions support the legislation?

Sasa Software Named multiple Winner of 2020 CDM InfoSec Awards
Sasa Software Wins “Content Disarm and Reconstruction (CDR)” AND “OT/ICS Security” awards announced at the 8th Annual CDM InfoSec Awards at #RSAC 2020
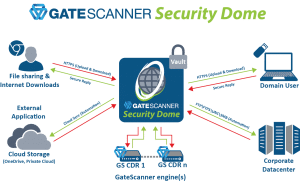
Announcing Gatescanner Security Dome Multi Route Content Disarm And Reconstruction As A Service Cdraas: Secure Your Digital Infrastructure
Launched at #RSAC 2020! GateScanner Security Dome protects multiple content delivery routes, all in one solution,
leveraging GateScanner® CDR to protect against weaponized content that has never been seen before.

Sasa Software Partners With Sentinelone To Offer Nextgen Ai Driven Security: Secure Your Digital Infrastructure
Sasa Software Partners with SentinelOne to Offer NextGen AI-driven Security First published on SentinelOne blog Content Disarm and Reconstruction (CDR) is designed to provide a safe, hassle-free solution for the prevention of file-based attacks. Instead of relying on signature-based scanning or sandbox behavioral analysis, the technology breaks the file into its components, and then re-creates

Sasa Software Has Partnered With Medone To Provide Global Cloud Services: Secure Your Digital Infrastructure
Together, we are offering GateScanner® Content Disarm and Reconstruction (CDR) solutions as a Service (CDRaaS = CDR as a Service), leveraging MedOne’s Next Generation cloud infrastructures for the highest level of performance, availability, and security.
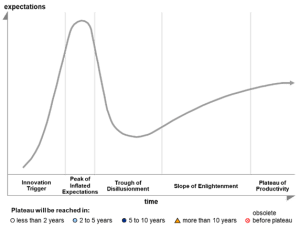
Sasa Software Recognized As Sample Vendor In Gartner Hype Cycle: Secure Your Digital Infrastructure
Gartner, the world’s leading research and advisory company, recently published the Hype Cycle for Threat-Facing Technologies, 2019, identifying Content Disarm and Reconstruction (CDR) on the Peak of Innovation phase of the Hype Cycle.

Portable Media Usb Security And Nerc Cip: Secure Your Digital Infrastructure
Industrial systems are under continuous threats- according to a recent study, Half of industrial control system networks have faced cyberattacks in the past year, and removable media (portable media) is identified as the second most common threats to these networks. The cyber threats emanating from USB devices are well documented…
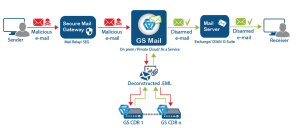
Caution: Can you trust external senders?
The CDR solution will then be able to open the encrypted file and handle its security In recent years, email has been increasingly used by hackers to initiate cyber-attacks. Email Attachments, unsecure links or phishing attacks provide hackers easy access to organizations. According to the Verizon Data Breach Investigation report (DBIR), nearly 50%* of APTs
GateScanner CDR Mail – Password Protected Attachments
In this video we’ll discuss a how GateScanner Mail CDR processes password protected attachments. Adding a password to files encrypts them, creating a challenge to scanning and detection technologies and opening a route of attack. GateScanner Mail CDR solves this with a unique capability for the user to securely provide the password for the file.

Israeli Cyber Researchers Demonstrate Hacking Of Siemens Simatic S7 Ics Controller: Secure Your Digital Infrastructure
Israeli Cyber researchers demonstrate hacking of Siemens Simatic S7 ICS controller.The vulnerability joins a stream of attacks against infrastructure and utilities, including the “LookBack” State-Nation sponsored malware attack, using a weaponized document to install a remote access Trojan (RAT) to potentially gain control of ICS networks.
Gatescanner Cdr Prevention Of Stenography Attacks: Secure Your Digital Infrastructure
In this session, we review how GateScanner Content Disarm and Reconstruction (CDR) prevents steganography (“stego”) attacks – hiding malware inside of files, and how GS CDR leverages NextGeneration AVs to detect and prevent the attacks.

Sasa Apac In Tech In Gov Canberra Aug 6 7th 19: Secure Your Digital Infrastructure
We are excited to announce launching our activities in Australia. Sasa APAC just kicked-off activities at the Tech in Gov conference in Canberra. Want to meet us? Contact us – We’re routinely visiting our Aussie customers and partners.

Sasa Software’s GateScanner successfully blocks ransomware attacks on Assuta Medical Centers
Sasa Software’s GateScanner solution successfully blocks ransomware attacks on Assuta Medical Centers March 1, 2017 Sasa Software’s security solutions, designed for the medical sector, have successfully prevented attacks on the Assuta hospital network. Among other things, sophisticated and unrecognized ransomware attacks were successfully blocked. Assuta – Medical Centers, the largest network of hospitals and medical
Shai-Hulud and the 2025 NPM Supply-Chain Worm: What the New Waves Mean — and Where CDR Fits In
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
When the Lights Go Out: The Hidden Risk of Zero-Day Attacks Timed With AV Update Blackouts — and Why Offline-Deterministic Protection Is Now Essential
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
Supply Chain Threats Inside Legitimate Content Feeds: An Escalating Cybersecurity Challenge
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
Code Embedded in Multimedia and Interactive Files: The New Malware Frontier
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
Encoded Malware in PDFs and Document Annotations
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
Ransomware Surge on SMBs: How Small Businesses Are Facing Big Threats and How GateScanner CDR Mitigates Them
As cybersecurity professionals gather for GovWare 2025, file-based threats remain one of cybersecurity’s most persistent “black holes.” Learn how intelligent threat elimination is revolutionizing file security.
Microsoft Teams Impersonation: How Matanbuchus 3.0 Is Delivered via Collaboration Tools — and How CDR Defeats It
As cybersecurity professionals gather for GovWare 2025, file-based threats remain one of cybersecurity’s most persistent “black holes.” Learn how intelligent threat elimination is revolutionizing file security.
Weaponized PDFs: How the new “MatrixPDF” toolkit works — and why native CDR stops it
As cybersecurity professionals gather for GovWare 2025, file-based threats remain one of cybersecurity’s most persistent “black holes.” Learn how intelligent threat elimination is revolutionizing file security.
What is a Zero-Day Exploit? Understanding the Hidden Cyber Threat
As cybersecurity professionals gather for GovWare 2025, file-based threats remain one of cybersecurity’s most persistent “black holes.” Learn how intelligent threat elimination is revolutionizing file security.
What Is a Polymorphic Virus? The Shape-Shifting Malware Threat
As cybersecurity professionals gather for GovWare 2025, file-based threats remain one of cybersecurity’s most persistent “black holes.” Learn how intelligent threat elimination is revolutionizing file security.
What Is Network Security? Your Complete Protection Guide
As cybersecurity professionals gather for GovWare 2025, file-based threats remain one of cybersecurity’s most persistent “black holes.” Learn how intelligent threat elimination is revolutionizing file security.
What is Operational Technology (OT)? A Complete Guide for 2025
As cybersecurity professionals gather for GovWare 2025, file-based threats remain one of cybersecurity’s most persistent “black holes.” Learn how intelligent threat elimination is revolutionizing file security.
What is Ransomware? Understanding the Modern Cyber Threat Landscape
As cybersecurity professionals gather for GovWare 2025, file-based threats remain one of cybersecurity’s most persistent “black holes.” Learn how intelligent threat elimination is revolutionizing file security.
Navigating the Last Frontiers of File-Based Cybersecurity
As cybersecurity professionals gather for GovWare 2025, file-based threats remain one of cybersecurity’s most persistent “black holes.” Learn how intelligent threat elimination is revolutionizing file security.
What are Executables and Why Are They a Threat?
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
Phishing Prevention Best Practices
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
Protect Your Company with Cloud Email Security
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
The Fundamentals of Data Redaction
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
What is Data Masking? A Complete Guide to Data Protection
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
What is Detection Evasion?
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
What is a Data Diode?
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
What are Cross Domain Solutions?
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
What is a Data Breach and How to Prevent It?
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
Advanced Persistent Threat: The Silent, Long-Term Cyberattack
Learn about Advanced Persistent Threats (APTs) – sophisticated cyberattacks that remain undetected for months. Discover detection strategies and defense methods.
The File-less Malware Misconception: Why “No Files” Doesn’t Mean No Malicious Files
File-less Malware Header MISCONCEPTION ALERT File-less ≠ No Files Why “file-less” malware still uses malicious files → MemoryPayload The term “file-less malware” has become a cybersecurity buzzword, often accompanied by dramatic claims about attacks that exist purely in memory without touching the disk. While this technology represents a significant evolution in attack techniques, the terminology
When a Picture Is Worth a Thousand Threats: The Hidden Dangers in PNG Files and the Power of Deep Content Inspection
Explore how attackers use innocent-looking PNG images to bypass traditional security and how deep content inspection (CDR) can prevent these stealthy threats.
Choosing the Right Email Security Solution: A Head-to-Head Comparison
In the ever-evolving landscape of cyber threats, email remains one of the most targeted and vulnerable attack vectors. Organizations looking to harden their defenses often turn to specialized email security solutions—but with so many options on the market, how do you choose the right one? Let’s break down key takeaways from a comparison of four
Spam Filter Gateway: The First Line of Defense Against Modern Email Threats
Spam Filter Gateway Banner Spam Filter Gateway: First Line Defense Essential cybersecurity infrastructure creating protective barriers between external email threats and internal systems. Filters malware, phishing, and social engineering attacks before reaching employee inboxes. Primary Attack Vector Protection – Email Security 99.9% Blocked Real-time Multi-layer Email Secured Spam filter gateways have become essential components of
Network Segregation: Building Resilient Security Architecture for the Modern Enterprise
Network Segregation Banner Network Segregation: Strategic Isolation Cornerstone of modern cybersecurity architecture. Compartmentalized network resources provide robust defense by containing breaches and protecting critical digital assets from sophisticated threats. Beyond Perimeter Security – Intelligent Containment Critical Finance HR Data Public Guest Segmented & Secure Network segregation has emerged as a cornerstone of modern cybersecurity architecture,
Business Email Compromise (BEC): Why These Social Engineering Attacks Are Costing Companies Millions
BEC Surgical Precision Banner BEC: Surgical Precision Targeted research. Personalized deception. Authentic urgency. Unlike broad phishing nets, BEC attacks are methodically crafted. Most Financially Damaging Cybercrime High Threat Business Email Compromise represents a growing threat to organizations worldwide, fundamentally different from traditional cyberattacks. Rather than exploiting technical vulnerabilities, BEC attacks manipulate human psychology and trust
Advanced Persistent Threat (APT): The Silent Cyber Predators Every Organization Must Understand
Introduction As we advance through 2025, the cybersecurity landscape is witnessing an unprecedented evolution in malware threats. The emergence of adaptive malware—malicious software enhanced with artificial intelligence capabilities—represents a paradigm shift in how cyber attacks are conducted and defended against. Unlike traditional malware that follows static, pre-defined instructions, adaptive malware continuously learns, evolves, and adapts
Unpacking the Threat: How Email Deconstruction Supercharges Virus Detection
Have you ever wondered what’s truly hidden inside the emails flooding your inbox?Beyond the visible text and attachments, emails are complex digital containers, often housing layers of hidden code and encoded content. This intricate structure, while facilitating rich communication, also provides a fertile ground for cyber attackers to conceal malicious payloads. To effectively combat these
WMI-based Attacks
Windows Management Instrumentation provides legitimate administrative capabilities that attackers leverage for covert operations, persistent access, and undetected lateral movement across enterprise networks.
In-memory Malware
In-memory malware operates exclusively within volatile system memory, using advanced techniques to avoid disk-based detection while maintaining persistent access and executing sophisticated attacks.
Lumma Stealer: Unmasking the Invisible Thief and Fortifying Your Defenses
In the evolving cybersecurity landscape, polymorphic and metamorphic malware represent the elite class of threats that continuously transform themselves to evade detection. This adaptive behavior is their defining characteristic and the primary reason they pose such significant threats to organizational security. While both types appear similar on the surface—constantly changing to avoid detection—their underlying mechanisms and capabilities differ substantially. Let’s explore these sophisticated threats and how to defend against them.
Adaptive Malware: The AI-Powered Threat Transforming Cybersecurity in 2025
In the evolving cybersecurity landscape, polymorphic and metamorphic malware represent the elite class of threats that continuously transform themselves to evade detection. This adaptive behavior is their defining characteristic and the primary reason they pose such significant threats to organizational security. While both types appear similar on the surface—constantly changing to avoid detection—their underlying mechanisms and capabilities differ substantially. Let’s explore these sophisticated threats and how to defend against them.
Understanding Polymorphic Malware: The Encryption Masters
In the evolving cybersecurity landscape, polymorphic and metamorphic malware represent the elite class of threats that continuously transform themselves to evade detection. This adaptive behavior is their defining characteristic and the primary reason they pose such significant threats to organizational security. While both types appear similar on the surface—constantly changing to avoid detection—their underlying mechanisms and capabilities differ substantially. Let’s explore these sophisticated threats and how to defend against them.
Why Managed File Transfer Outperforms SFTP for Modern Business Security
The Evolving File Transfer Landscape In today’s digital business environment, secure file transfer capabilities have become mission-critical. Organizations exchange sensitive information with partners, customers, and across internal systems daily, often transferring gigabytes of data containing proprietary information, customer records, and other valuable assets. The stakes couldn’t be higher – according to recent data, the global
The AI Phishing Revolution: Implications for Cybersecurity in 2025
The Changing Face of Phishing Artificial intelligence has dramatically transformed the cybersecurity landscape of 2025. Where once phishing attacks were characterized by obvious grammatical errors and crude personalization attempts, today’s AI-powered phishing campaigns present a sophisticated threat that challenges traditional security measures. This evolution presents both unprecedented challenges and opportunities for organizations committed to protecting
Living off the Land (LotL) Attacks
Living off the Land attacks weaponize legitimate system administration tools for malicious purposes, making detection extremely challenging as attackers blend with normal operations.
Fileless Malware
Fileless malware represents a paradigm shift in cyber threats, executing entirely within system memory while leveraging legitimate tools to evade traditional security controls.
PowerShell & Scripting Abuse in Fileless Attacks
Attackers increasingly weaponize PowerShell and scripting languages to execute fileless attacks, leveraging legitimate administrative tools to bypass security controls and establish persistent access.
How Fileless Threats Bypass Antivirus
Fileless threats exploit fundamental limitations in traditional antivirus architecture, operating entirely in memory and leveraging legitimate tools to evade signature-based detection mechanisms.
Best Practices to Prevent Fileless Attacks
Preventing fileless attacks requires a multi-layered security approach combining technical controls, policy enforcement, and continuous monitoring to eliminate memory-based threat vectors.
How to Detect Fileless Malware
Fileless malware detection requires advanced techniques beyond traditional signature-based approaches, focusing on behavioral analysis, memory forensics, and sophisticated monitoring systems.
Common Entry Points for File-less Attacks
File-less attacks exploit specific vulnerabilities and access points to gain initial foothold in target systems without traditional file-based detection signatures.
Fileless Attacks vs Traditional Malware
Understanding the fundamental differences between fileless attacks and traditional malware is crucial for implementing effective defense strategies in today’s evolving threat landscape.
How Fileless Malware Works
Fileless malware operates entirely in system memory, using legitimate tools and processes to establish persistence and evade detection through sophisticated technical mechanisms.
Fileless Attacks: The Invisible Cyber Threat
Fileless attacks leverage legitimate system tools and reside only in memory, making them incredibly difficult to detect using traditional antivirus and file-based security solutions.
Behind the Scenes: What Does ‘Safely Remove a USB’ Actually Do?
Discover the critical processes that occur when you safely eject removable media and why skipping this step can risk data corruption, drive damage, and security vulnerabilities.
Defending Your Digital Boundaries: Understanding Removable Media Protection
Removable media protection encompasses the policies, procedures, and technologies that secure organizations against the unique threats posed by portable storage devices.
Balancing Convenience and Protection: Understanding BYOD in Cybersecurity
BYOD introduces significant security risks as personal devices access corporate resources. Effective management requires balancing employee experience with robust protection measures.
Securing Your Physical Endpoints: Understanding USB Blockers
USB blockers provide tangible protection against unauthorized device connections through physical port security that complements software-based controls in your security strategy.
Defending Your Digital Perimeter: Understanding USB Lockdown Software
USB lockdown software offers crucial protection against unauthorized devices by controlling, monitoring, and securing removable media access across your organization.
Defending Your Digital Assets: Effective Removable Media Protection Strategies
Learn how to implement multi-layered defense against removable media threats through comprehensive policies, advanced technologies, and ongoing security awareness.
Securing Your Digital Perimeter: Implementing Effective USB Port Lockdown Policies
Discover practical strategies for creating and enforcing USB port lockdown policies that balance strong security controls with business functionality across your enterprise.
Protecting Your Enterprise: Essential USB Safety Best Practices
Discover proven strategies to secure your organization against USB-based threats while maintaining productivity through proper policies, tools, and user education.
Safeguarding Your Systems: Essential USB Blocking Techniques and Tools
Discover practical methods to control USB device access and protect your organization’s network from removable media threats using physical, administrative, and software-based approaches.
Navigating the Hidden Dangers: BYOD Security Risks Explained
While BYOD policies boost productivity and employee satisfaction, they create significant security vulnerabilities that organizations must address through comprehensive management strategies.
Hidden Dangers: The Cybersecurity Risks of Removable Media
Removable media devices present significant security vulnerabilities that can lead to data breaches, malware infections, and regulatory violations if not properly managed.
Securing the Digital Perimeter: Understanding USB Port Lockdown
USB port lockdown strategies prevent unauthorized devices from connecting to your network, mitigating risks from malware, data theft, and other threat vectors.
Protecting Your Organization’s Digital Gateways: Understanding USB Port Security
USB ports represent significant entry points for cyber threats. Learn how comprehensive USB port security measures can safeguard your organization’s sensitive data and systems.
Secure File Gateways: The First Line of Defense Against File-Based Threats
Secure file gateways provide advanced protection against file-based threats by combining deep content inspection, sanitization technologies, and policy enforcement to ensure only safe files enter organizational networks.
Cross-Platform Storage Access: Breaking Down Enterprise Data Barriers
Cross-platform storage access technologies enable organizations to provide consistent, secure data availability across different operating systems, devices, and environments while maintaining governance and control.
Centralized Storage Interfaces: Simplifying Enterprise Data Management
Centralized storage interfaces provide a unified platform for accessing, managing, and securing enterprise data across diverse storage systems, locations, and formats while simplifying administration and enhancing security.
HTTPS File Transfer: Secure Web-Based Data Exchange Explained
HTTPS file transfer leverages the web’s universal protocol with TLS encryption to provide secure, accessible, and firewall-friendly file exchange that works seamlessly across platforms, browsers, and devices.
SFTP Explained: The Foundation of Secure File Transfer
SFTP (SSH File Transfer Protocol) provides robust security for file transfers through encryption, strong authentication, and comprehensive file operations while offering excellent compatibility across platforms.
Cloud vs. On-Premise MFT: Making the Strategic Deployment Decision
Selecting between cloud and on-premise MFT deployment models requires careful evaluation of security requirements, compliance needs, IT resources, scalability demands, and total cost of ownership.
File Transfer Automation: Streamlining Critical Data Exchange Processes
Selecting the right Managed File Transfer solution requires careful evaluation of security capabilities, scalability, integration options, compliance features, and total cost of ownership aligned with your organization’s unique requirements.
Selecting Your Ideal MFT Solution: A Strategic Evaluation Framework
Selecting the right Managed File Transfer solution requires careful evaluation of security capabilities, scalability, integration options, compliance features, and total cost of ownership aligned with your organization’s unique requirements.
MFT Security: Essential Practices for Enterprise Data Protection
Implementing robust security measures for Managed File Transfer systems is essential for protecting sensitive data, maintaining regulatory compliance, and preserving business reputation in today’s threat landscape.
Secure File Transfer Protocols: The Backbone of Protected Data Exchange
Secure file transfer protocols provide the essential infrastructure for protected data exchange, each offering distinct security features, performance characteristics, and compliance capabilities.
File Transfer Automation: Transforming Enterprise Data Exchange
Automated file transfer solutions eliminate manual processes, reduce human error, and provide robust security and compliance features that protect sensitive data throughout its journey.
Zero-Day Malware in 2025: Defending Against the Unknown
In today’s rapidly evolving threat landscape, zero day malware represents one of the most formidable challenges facing organizations worldwide. Unlike conventional threats that can be identified by signature-based detection methods, zero-day malware operates entirely below the radar—unknown to security vendors and undetectable by traditional scanning technologies. These sophisticated threats exploit the gap between malware innovation
Security Blind Spots: Understanding and Blocking Advanced SEG Evasion Tactics
Explore how cybercriminals systematically test and evade Secure Email Gateway defenses, and discover the advanced countermeasures that keep organizations one step ahead of evolving threats.
Beyond the Surface: How Deep Content Inspection Uncovers Hidden Threats
Discover how Deep Content Inspection technologies dissect and analyze files at their most fundamental level to detect sophisticated threats that evade traditional security solutions.
Email Sandboxing’s Dynamic Defense Against Zero-Day Threats
Discover how email sandboxing technology creates controlled environments to execute suspicious attachments and links, exposing malicious behavior before threats can reach your network.
From Hook to Shield: Modern Approaches to Phishing Prevention
Discover the multi-layered strategies organizations use to defend against phishing attacks that continue to evolve in sophistication and remain the leading cause of security breaches.
Email Threat Protection: Your Digital Shield Against Advanced Email Attacks
Discover how Email Threat Protection solutions defend organizations from phishing, malware, business email compromise, and other sophisticated threats targeting your most vulnerable communication channel
The Compliance Shield: Secure Email Gateways in Today’s Regulatory Landscape
Learn how Secure Email Gateways provide essential capabilities for meeting regulatory requirements while protecting sensitive data from increasingly sophisticated email-based threats.
Choosing Between On-Premise and Cloud Email Security
Understand the key differences, advantages, and considerations for both on-premise and cloud-based Secure Email Gateway deployments to make an informed choice for your organization.
When Email Attacks: The Cascading Costs That Security Budgets Miss
Learn why email-based attacks cost organizations far more than just ransom payments or stolen funds, and how Secure Email Gateways provide essential protection against these multifaceted threats.
What is File Hashing in Cybersecurity? Understanding Digital Fingerprints
File hashing is a security technique that generates a unique fingerprint for files, helping to detect tampered or malicious content.
What is a Malicious Macro? Understanding Document-Based Threats
A malicious macro is a script embedded in documents (e.g., Word or Excel files) that automatically executes harmful actions when opened.
What is Remote Code Execution (RCE)? Understanding the Ultimate Cyber Threat
A malicious macro is a script embedded in documents (e.g., Word or Excel files) that automatically executes harmful actions when opened.
Secure Managed File Transfer (MFT): Enterprise-Grade Protection for Critical Data Exchange
Discover how Secure Managed File Transfer solutions enable organizations to exchange sensitive information with enhanced security, automation, compliance, and visibility.
What is a Drive-By Download? Infections Without Interaction
RCE is a cyberattack that allows hackers to execute malicious code remotely on a victim’s device, often through file-based exploits.
What is a Payload in Cybersecurity? Understanding the Malicious Core
A payload is the malicious component of an attack, such as ransomware or spyware, that executes once a file-based exploit is triggered.
Secure File Transfer: Protecting Your Data in Motion
Secure file transfer technologies provide robust protection for sensitive data in transit, preventing unauthorized access and ensuring compliance with data security regulations.
What is an Exploit File? Understanding the Digital Lockpick
An exploit file is a document or executable that takes advantage of software vulnerabilities to install malware or gain unauthorized access.
What is Spear Phishing? The Art of Targeted Deception
Spear phishing is a highly targeted phishing attack where attackers impersonate trusted contacts to deceive victims into opening malicious files or links.
Gateway or Cloud? Navigating the Modern Email Security Landscape
Understand the key differences between traditional Secure Email Gateways and emerging Cloud Email Security solutions to make informed decisions about protecting your organization’s communications.
Beyond Pattern Matching: How Email Security Became an Intelligent Guardian
Trace the transformation of email security technology from rudimentary spam blockers to today’s sophisticated AI-powered systems that protect organizations from advanced threats.
Stopping Ransomware at the Gateway: The Critical Email Security Advantage
Discover how modern Secure Email Gateways detect and neutralize sophisticated ransomware delivery mechanisms before they can infiltrate your network and encrypt critical systems.
Breaking the BEC Chain: Modern SEG Tactics Against Financial Fraud
Discover how modern Secure Email Gateways employ advanced detection techniques to identify and block Business Email Compromise attacks that cost organizations billions annually.
Separating Substance from Marketing: What Makes File Security Truly Deep
In the cybersecurity industry, terminology often becomes a battleground where marketing creativity competes with technical reality. Recent years have seen the emergence of terminology suggesting certain Content Disarm and Reconstruction (CDR) solutions penetrate file structures more “deeply” than others. CDR technology, by its very nature, should always be thorough and comprehensive regardless of marketing qualifiers.
Malicious Installer Packages: A Trojan Horse for Cyber Threats
Cybercriminals disguise malware as legitimate software installers, tricking users into downloading and executing malicious payloads.
What Are Unknown Threats? Understanding the Cybersecurity Blindspots
Unknown threats refer to new or undetected cyber threats that security tools fail to recognize due to their novel techniques or lack of prior signatures.
How ISO and Archive Files Are Used for Malware Delivery
Attackers often embed malware in ISO and archive files like ZIP and RAR, using them to bypass email security filters and execute malicious code.
Payload Obfuscation: How Attackers Hide Malware
Hackers use encryption, encoding, and other techniques to hide malware payloads within files, evading traditional detection methods.

