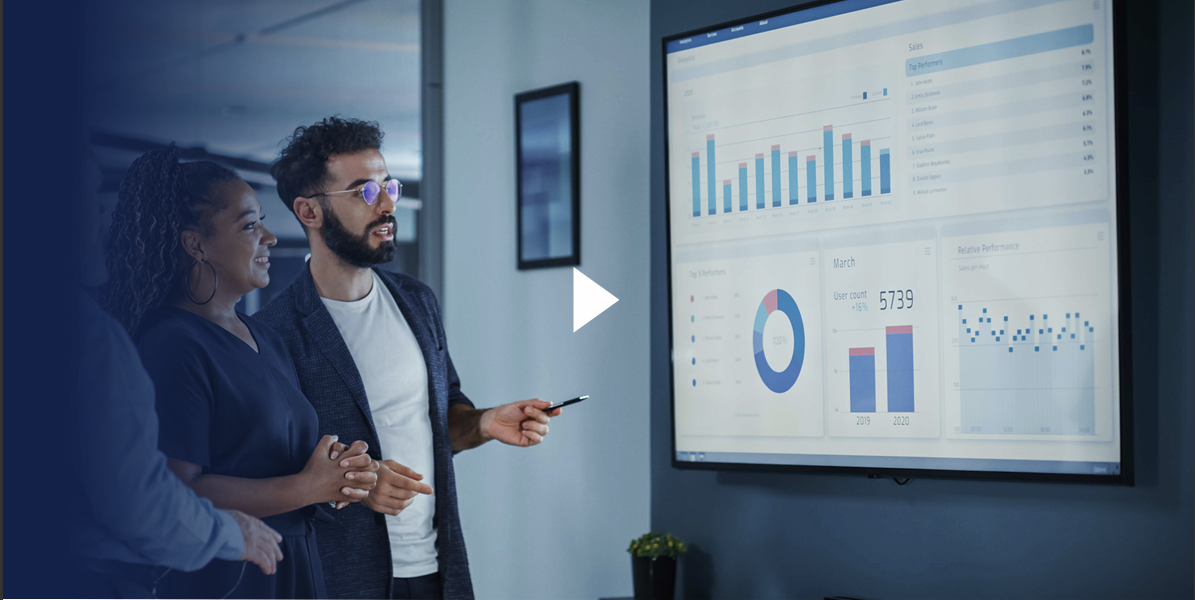
Protecting Networks From File Based Attacks
GateScanner®: Your Network’s Ultimate Defense Against File-Based Attacks.
Threat-free files and emails, delivered seamlessly.

Protecting Networks From File Based Attacks
GateScanner®: Your Network’s Ultimate Defense Against File-Based Attacks. Threat-free files, delivered seamlessly.
Prevention On Every Channel
How GateScanner Works
GateScanner detoxifies each and every incoming file, email and attachment, removing both known, as well as previously unseen (‘signature-less’) malware





Protecting The Workspace From Threats
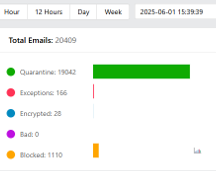
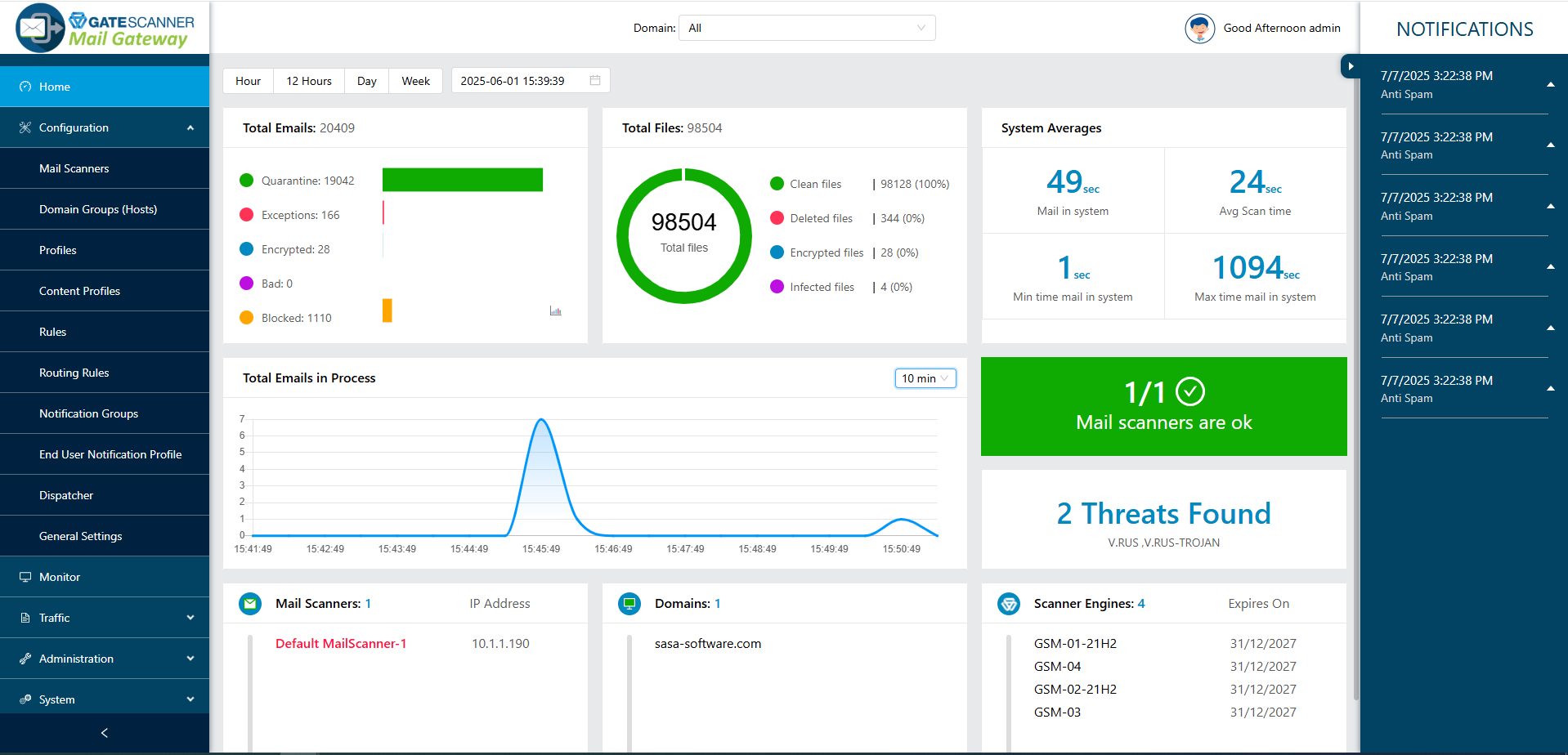
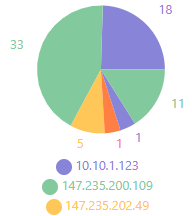
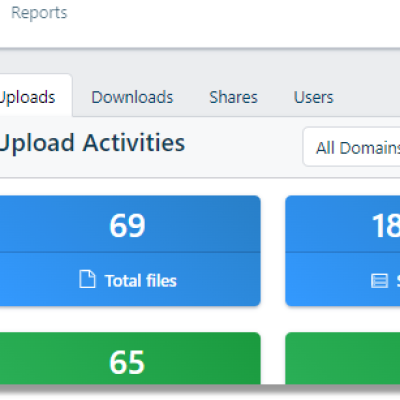
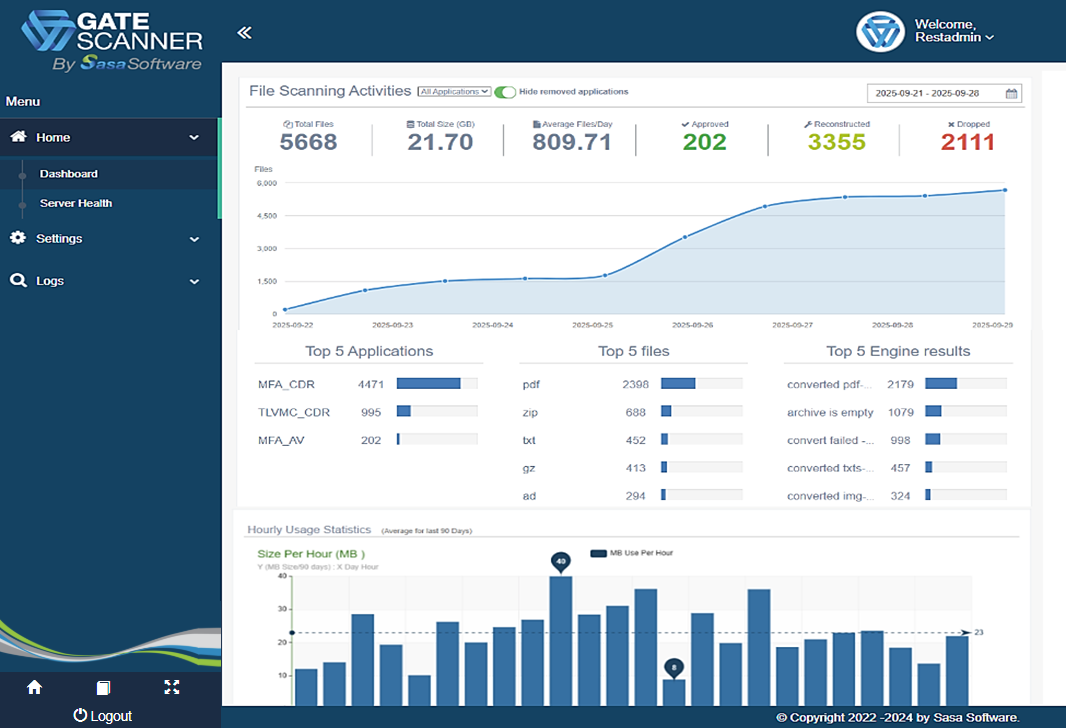
Unified Security Dashboard
Historical and real-time email processing details with drill-down
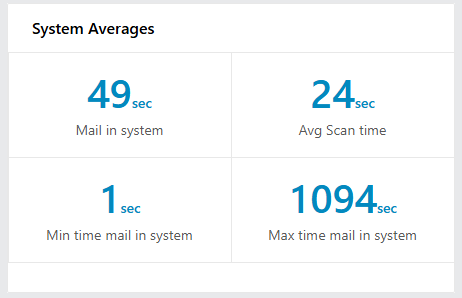
System Performance and Health
System state and throughput at a glance
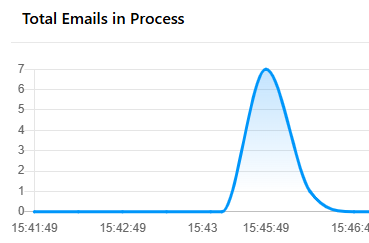
Real time Mails-in-Process Monitoring
Catch anomalies as they occur
Security Dome: Enterprise MFT with Native CDR Security
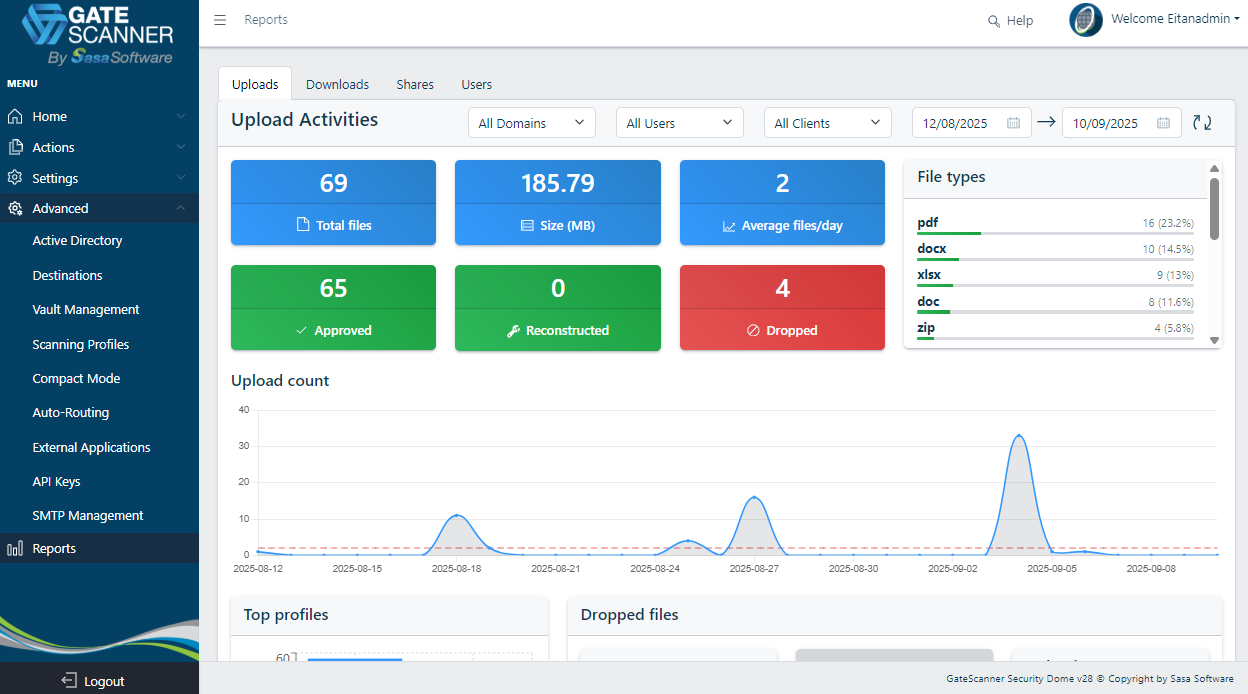
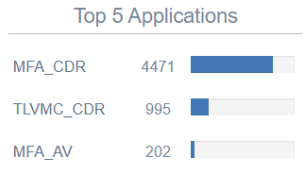
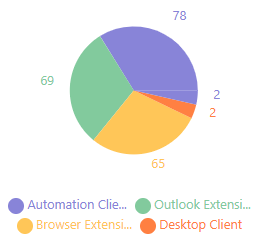
Most Active Applications
Monitor your most active file sanitization consumers

Hourly Usage
Detect unusual data transfer patterns that may indicate exfiltration or attack campaigns.

CDR Engine Results
Monitor sanitization effectiveness and identify problematic file patterns requiring attention.
Trusted by Leading Organizations
GateScanner CDR technology is protecting over 450 critical networks globally
in financial services, energy, industry, healthcare, transportation, defense and infrastructure.




















Zero-Trust file security

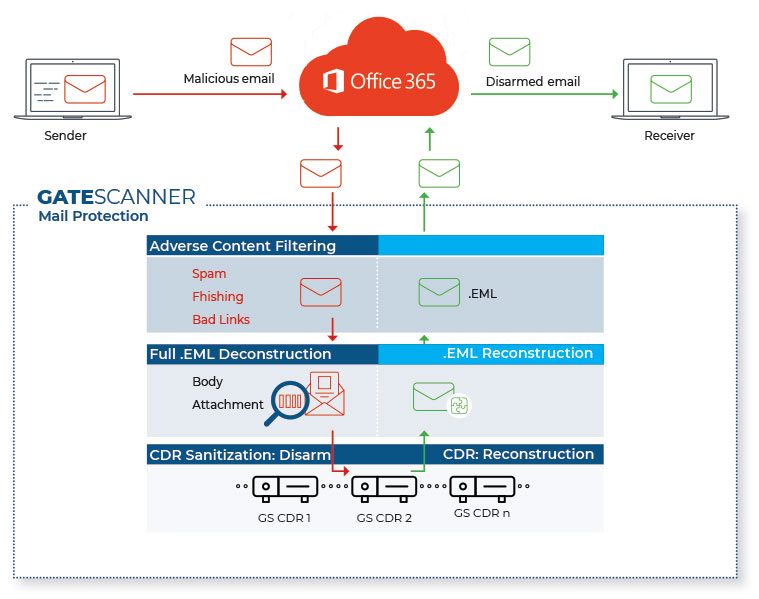
Email Gateway Protection

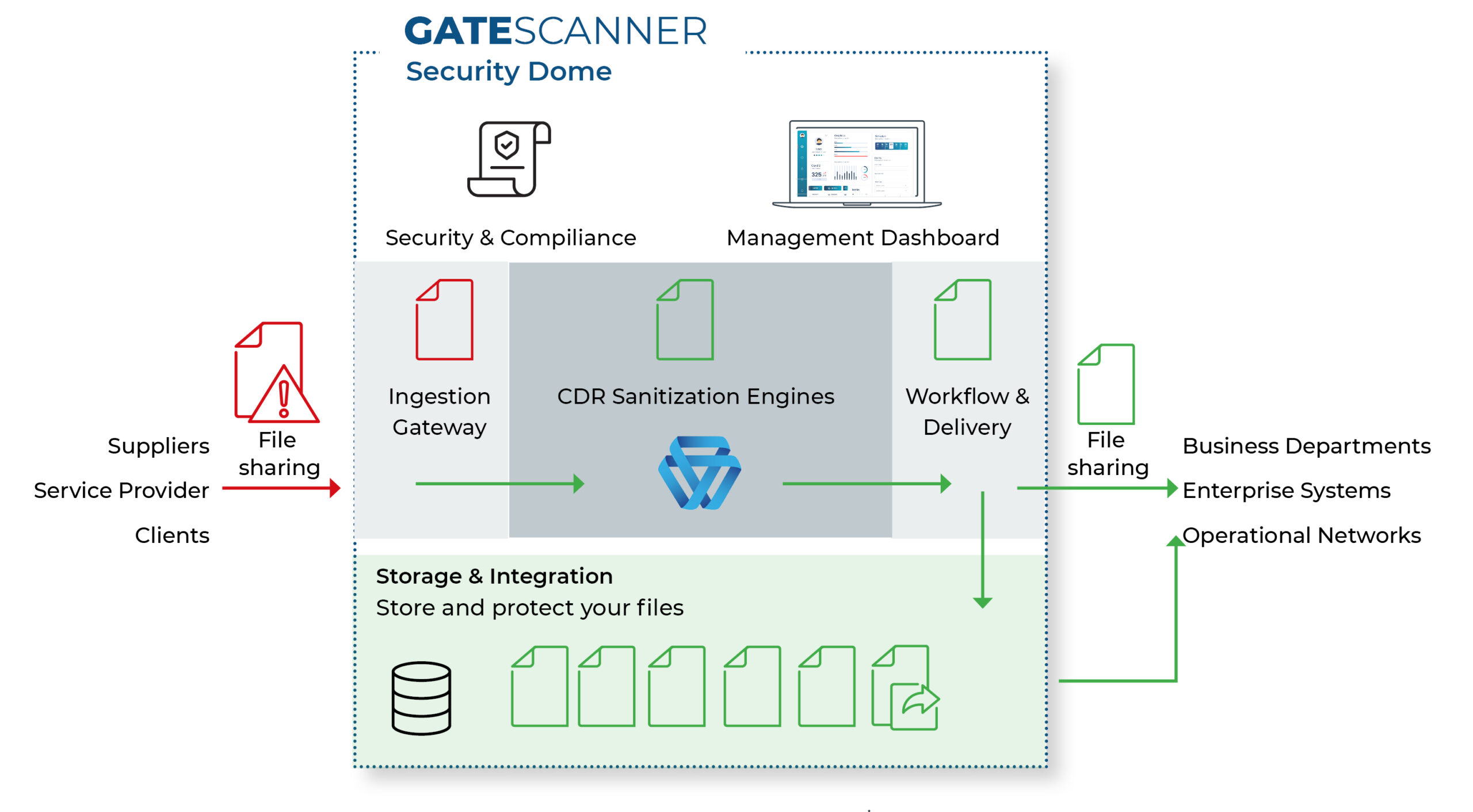
Third-Party Document Exchange

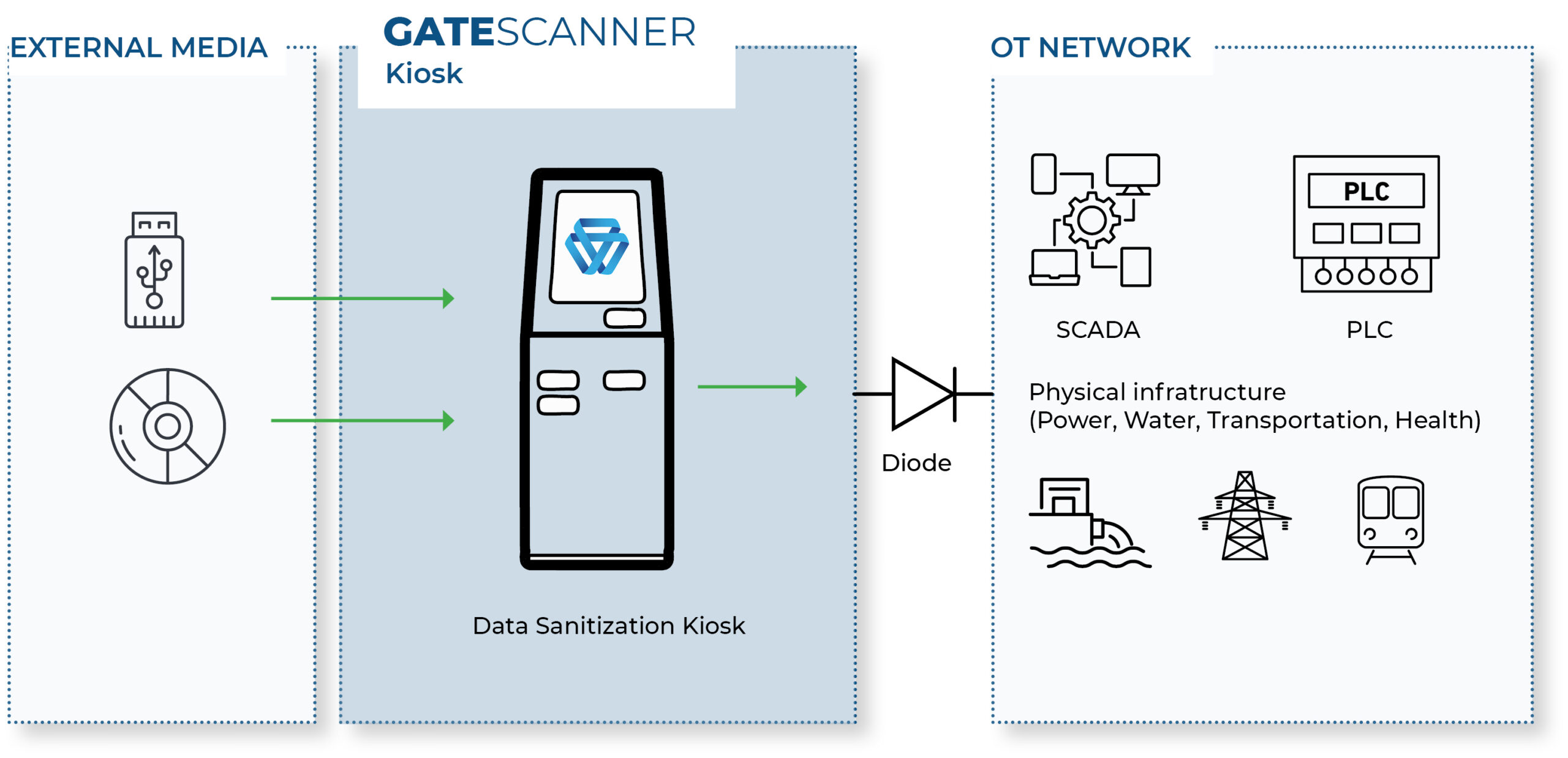
Air-Gapped Network File Transfer


Critical Infrastructure Protection
Email Gateway Protection

Third-Party Document Exchange

Air-Gapped Network File Transfer

Critical Infrastructure Protection