GATESCANNER
First in File Security
Most network attacks gain initial access through incoming content.
GateScanner blocks all incoming malicious content in email and files
GATESCANNER blocks all malicious content arriving in emails and files – including unknown, zero-hour malware – without detection.
including unknown, zero-hour malware – without detection
using Content Disarm & Reconstruction (CDR) technology
GateScanner - Prevents the Undetectable
HOW GATESCANNER WORKS
DE-CONSTRUCTION
RE-CONSTRUCTION
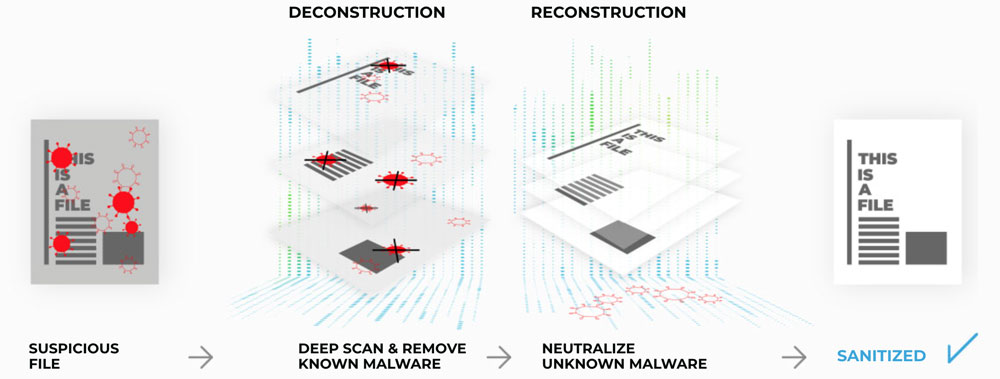
SUSPICIOUS FILE
DEEP SCAN & REMOVE KNOWN MALWARE
NEUTRALIZE UNKNOWN MALWARE
SANITIZED
Detection-based AV’s fail to detect highly obfuscated and zero-day malware in emails and files.
Content Disarm and Reconstruction (CDR) transforms content
to neutralize threats before they reach the endpoints.
GateSCanner
Trust Your Files
proven protection






Gartner Disclaimer: The GARTNER COOL VENDOR badge is a trademark and service mark of Gartner, Inc. and/or its affiliates and is used herein with permission. All rights reserved. Gartner does not endorse any vendor, product or service depicted in its research publications and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s Research & Advisory organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
CDR file sanitization
prevention on every channel
Email Security done right
Inline
Data Security
Secure MFT
Secure
Web downloads
Portable Media Security
75% of all successful network attacks start with a bad email. Phishing, toxic URL’s toxic attachments and hidden code …
Data can be compromised at many points along its path.
File sanitization inserted via API/ICAP provides unparalleled flexibility…
Supply chain
attacks delivered through shared content, arriving on proliferation of connected services, is a major threat …
The Internet is rife with threats. Any clickable link can lead to a malicious download endangering …
USB sticks are
found everywhere – and are an easy medium through which criminals infiltrate networks.
CDR file sanitization
prevention on every channel
Email Security done right
75% of all successful network attacks start with a bad email. Phishing, toxic URL’s toxic attachments and hidden code …
Inline
Data Security
Data can be compromised at many points along its path through the network.
File sanitization inserted via API/ICAP provides unparalleled flexibility…
Secure MFT
Supply chain
attacks delivered through shared content, arriving on proliferation of connected services, is a major threat …
Secure
Web downloads
The Internet is rife with threats. Any clickable link can lead to a malicious download endangering …
Portable Media Security
USB sticks are
found everywhere – and are an easy medium through which criminals infiltrate networks…
REQUEST A DEMO
Let us show you GateScanner in action
WE PROTECT THEM TOO
LONG TERM CLIENTS












































BUILT TO PROTECT
Initially developed to protect a U.S. Army contractor in northern Israel, GateScanner is designed to perform in extremely high-threat environments.
GateScanner has become the choice of top government, infrastructure and enterprise networks around the world.


